China’s Unrestricted Warfare Against the U.S.
BY Herschel SmithJust nosy snooping, or something larger?
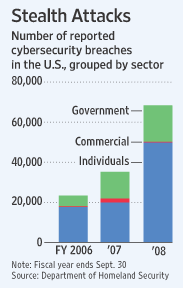
Cyberspies have penetrated the U.S. electrical grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials.
The spies came from China, Russia and other countries, these officials said, and were believed to be on a mission to navigate the U.S. electrical system and its controls. The intruders haven’t sought to damage the power grid or other key infrastructure, but officials warned they could try during a crisis or war.
“The Chinese have attempted to map our infrastructure, such as the electrical grid,” said a senior intelligence official. “So have the Russians.”
The espionage appeared pervasive across the U.S. and doesn’t target a particular company or region, said a former Department of Homeland Security official. “There are intrusions, and they are growing,” the former official said, referring to electrical systems. “There were a lot last year.”
Many of the intrusions were detected not by the companies in charge of the infrastructure but by U.S. intelligence agencies, officials said. Intelligence officials worry about cyber attackers taking control of electrical facilities, a nuclear power plant or financial networks via the Internet.
Authorities investigating the intrusions have found software tools left behind that could be used to destroy infrastructure components, the senior intelligence official said. He added, “If we go to war with them, they will try to turn them on.”
Officials said water, sewage and other infrastructure systems also were at risk.
“Over the past several years, we have seen cyberattacks against critical infrastructures abroad, and many of our own infrastructures are as vulnerable as their foreign counterparts,” Director of National Intelligence Dennis Blair recently told lawmakers. “A number of nations, including Russia and China, can disrupt elements of the U.S. information infrastructure.”
The concerns about nuclear reactors being controlled from software is an overreach, since the plant operators and control systems are the only ones who have direct control over plant components. However, the balance of the concerns are salient.
This is much more than nosy snooping, although there is no need to exonerate nosy snooping either. In 1999 two Colonels in the Chinese Army, Qiao Liang and Wang Xiangsui, authored a study entitled Unrestricted Warfare. In it, they argued that while conventional warfare had become too costly in terms of its financial and political ramifications, rather than relying on direct military confrontation alone, other means must be employed to defeat the U.S. These include lawfare and political pressure, network warfare and terrorism, among other means. The entire study is worth reading.
What is being witnessed is network warfare. It’s more than just stealing proprietary information and technological secrets (although they have indeed managed to obtain some very important technology in miniturization of nuclear weapons). This goes to actual warfare, although not of the kind the public typically thinks of when considering war.
But it is no less dangerous, hostile and intended for harm. If you doubt this, consider a nation without electricity, water, banking, refrigeration, and traffic signals. Now consider the fact that China is pursuing an aircraft carrier, is flexing its muscle in its littorals, and is designing UAVs for the purpose of “military aerial inspection and detection, electronic warfare and other missions.”
Trackbacks & Pingbacks
Comments
RSS feed for comments on this post. TrackBack URL
Leave a comment