Computer spies have broken into the Pentagon’s $300 billion Joint Strike Fighter project — the Defense Department’s costliest weapons program ever — according to current and former government officials familiar with the attacks.
Similar incidents have also breached the Air Force’s air-traffic-control system in recent months, these people say. In the case of the fighter-jet program, the intruders were able to copy and siphon off several terabytes of data related to design and electronics systems, officials say, potentially making it easier to defend against the craft.
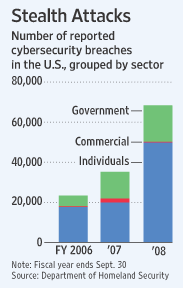
The latest intrusions provide new evidence that a battle is heating up between the U.S. and potential adversaries over the data networks that tie the world together. The revelations follow a recent Wall Street Journal report that computers used to control the U.S. electrical-distribution system, as well as other infrastructure, have also been infiltrated by spies abroad.
Attacks like these — or U.S. awareness of them — appear to have escalated in the past six months, said one former official briefed on the matter. “There’s never been anything like it,” this person said, adding that other military and civilian agencies as well as private companies are affected. “It’s everything that keeps this country going.”
Many details couldn’t be learned, including the specific identity of the attackers, and the scope of the damage to the U.S. defense program, either in financial or security terms. In addition, while the spies were able to download sizable amounts of data related to the jet-fighter, they weren’t able to access the most sensitive material, which is stored on computers not connected to the Internet.
Former U.S. officials say the attacks appear to have originated in China. However it can be extremely difficult to determine the true origin because it is easy to mask identities online.
A Pentagon report issued last month said that the Chinese military has made “steady progress” in developing online-warfare techniques. China hopes its computer skills can help it compensate for an underdeveloped military, the report said.
The Chinese Embassy said in a statement that China “opposes and forbids all forms of cyber crimes.” It called the Pentagon’s report “a product of the Cold War mentality” and said the allegations of cyber espionage are “intentionally fabricated to fan up China threat sensations.”
The U.S. has no single government or military office responsible for cyber security. The Obama administration is likely to soon propose creating a senior White House computer-security post to coordinate policy and a new military command that would take the lead in protecting key computer networks from intrusions, according to senior officials.
The Bush administration planned to spend about $17 billion over several years on a new online-security initiative and the Obama administration has indicated it could expand on that. Spending on this scale would represent a potential windfall for government agencies and private contractors at a time of falling budgets. While specialists broadly agree that the threat is growing, there is debate about how much to spend in defending against attacks.
The Joint Strike Fighter, also known as the F-35 Lightning II, is the costliest and most technically challenging weapons program the Pentagon has ever attempted. The plane, led by Lockheed Martin Corp., relies on 7.5 million lines of computer code, which the Government Accountability Office said is more than triple the amount used in the current top Air Force fighter.
Six current and former officials familiar with the matter confirmed that the fighter program had been repeatedly broken into. The Air Force has launched an investigation.
Pentagon officials declined to comment directly on the Joint Strike Fighter compromises. Pentagon systems “are probed daily,” said Air Force Lt. Col. Eric Butterbaugh, a Pentagon spokesman. “We aggressively monitor our networks for intrusions and have appropriate procedures to address these threats.” U.S. counterintelligence chief Joel Brenner, speaking earlier this month to a business audience in Austin, Texas, warned that fighter-jet programs have been compromised.
Foreign allies are helping develop the aircraft, which opens up other avenues of attack for spies online. At least one breach appears to have occurred in Turkey and another country that is a U.S. ally, according to people familiar with the matter.
Joint Strike Fighter test aircraft are already flying, and money to build the jet is included in the Pentagon’s budget for this year and next.
Computer systems involved with the program appear to have been infiltrated at least as far back as 2007, according to people familiar with the matter. Evidence of penetrations continued to be discovered at least into 2008. The intruders appear to have been interested in data about the design of the plane, its performance statistics and its electronic systems, former officials said.
The intruders compromised the system responsible for diagnosing a plane’s maintenance problems during flight, according to officials familiar with the matter. However, the plane’s most vital systems — such as flight controls and sensors — are physically isolated from the publicly accessible Internet, they said.
The intruders entered through vulnerabilities in the networks of two or three contractors helping to build the high-tech fighter jet, according to people who have been briefed on the matter. Lockheed Martin is the lead contractor on the program, and Northrop Grumman Corp. and BAE Systems PLC also play major roles in its development.
Lockheed Martin and BAE declined to comment. Northrop referred questions to Lockheed. Cyberspies have penetrated the U.S. electrical grid and left behind software programs that could be used to disrupt the system, according to current and former national-security officials.
The spies came from China, Russia and other countries, these officials said, and were believed to be on a mission to navigate the U.S. electrical system and its controls. The intruders haven’t sought to damage the power grid or other key infrastructure, but officials warned they could try during a crisis or war.
“The Chinese have attempted to map our infrastructure, such as the electrical grid,” said a senior intelligence official. “So have the Russians.”
The espionage appeared pervasive across the U.S. and doesn’t target a particular company or region, said a former Department of Homeland Security official. “There are intrusions, and they are growing,” the former official said, referring to electrical systems. “There were a lot last year.”
Shame on Northrop Grumman and Lockheed for their lack of control over their IT systems, and the Pentagon response is lousy as well. Sure the Pentagon systems are probed daily. That’s not the point. China is currently in unrestricted warfare against the U.S.. and this aggresive pattern requires a robust response. How long will we continue to make technology available to China, either through system vulnerabilities or intentional commercial technology transfer?