We’ve seen how the Department of Homeland Security has pressed for biometric identification of American citizens, and how American police have adopted COIN tactics, techniques and procedures in the policing of America, including more than seventy federal agencies. These are cogs in a larger machine. In an event that went completed ignored in the Main Stream Media (ignored, not missed), Wikileaks recently released 249 important documents on global intelligence contractors.
Today, Wednesday 4 September 2013 at 1600 UTC, WikiLeaks released ‘Spy Files #3′ – 249 documents from 92 global intelligence contractors. These documents reveal how, as the intelligence world has privatised, US, EU and developing world intelligence agencies have rushed into spending millions on next-generation mass surveillance technology to target communities, groups and whole populations.
WikiLeaks’ publisher Julian Assange stated: “WikiLeaks’ Spy Files #3 is part of our ongoing commitment to shining a light on the secretive mass surveillance industry. This publication doubles the WikiLeaks Spy Files database. The WikiLeaks Spy Files form a valuable resource for journalists and citizens alike, detailing and explaining how secretive state intelligence agencies are merging with the corporate world in their bid to harvest all human electronic communication.”
WikiLeaks’ Counter Intelligence Unit has been tracking the trackers. The WLCIU has collected data on the movements of key players in the surveillance contractor industry, including senior employees of Gamma, Hacking Team and others as they travel through Azerbaijan, Bahrain, Brazil, Spain, Mexico and other countries.
Julian Assange, WikiLeaks’ publisher, stated: “The WikiLeaks Counter Intelligence Unit operates to defend WikiLeaks’ assets, staff and sources, and, more broadly, to counter threats against investigative journalism and the public’s right to know.”
Documents in Spy Files #3 include sensitive sales brochures and presentations used to woo state intelligence agencies into buying mass surveillance services and technologies. Spy Files #3 also includes contracts and deployment documents, detailing specifics on how certain systems are installed and operated.
Internet spying technologies now being sold on the intelligence market include detecting encrypted and obfuscated internet usage such as Skype, BitTorrent, VPN, SSH and SSL. The documents reveal how contractors work with intelligence and policing agencies to obtain decryption keys.
The documents also detail bulk interception methods for voice, SMS, MMS, email, fax and satellite phone communications. The released documents also show intelligence contractors selling the ability to analyse web and mobile interceptions in real-time.
Analysis & Commentary
An important reddit comment follows this up.
Would you like to know more?
Revolution in Military Affairs
http://en.m.wikipedia.org/wiki/Revolution_in_Military_Affairs
Former DoD analyst Franklin Spinney
http://en.m.wikipedia.org/wiki/Franklin_C._Spinney
“At the core of the RMA is a radical hypothesis that would cause Sun Tzu, Clausewitz and George Patton to roll over in their graves. That is, that technology will transform the fog and friction of combat – the uncertainty, fear, chaos, imperfect information which is a natural product of a clash between opposing wills – into clear, friction-free, predictable, mechanistic interaction.”
Project for the New American Century
http://en.wikipedia.org/wiki/Project_for_the_New_American_Century
In its “Preface”, in highlighted boxes, Rebuilding America’s Defenses states that it aims to:
ESTABLISH FOUR CORE MISSIONS for the U.S. military:
- Defend the American homeland;
- Fight and decisively win multiple, simultaneous major theater wars;
- Perform the “constabulary” duties associated with shaping the security environment in critical regions;
- Transform U.S. forces to exploit the “revolution in military affairs”;
CONTROL THE NEW “INTERNATIONAL COMMONS” OF SPACE AND “CYBERSPACE”
Section V of Rebuilding America’s Defenses, entitled “Creating Tomorrow’s Dominant Force”, includes the sentence: “Further, the process of transformation, even if it brings revolutionary change, is likely to be a long one, absent some catastrophic and catalyzing event––like a new Pearl Harbor” (51).[15]
“The technotronic era involves the gradual appearance of a more controlled society. Such a society would be dominated by an elite, unrestrained by traditional values. Soon it will be possible to assert almost continuous surveillance over every citizen and maintain up-to-date complete files containing even the most personal information about the citizen. These files will be subject to instantaneous retrieval by the authorities. ”
-Zbigniew Brzezinski, geopolitician, former US National Security Advisor, and member of the Bilderberg Group. Quote lifted from his book “Between Two Ages”
http://en.m.wikipedia.org/wiki/Zbigniew_Brzezinski
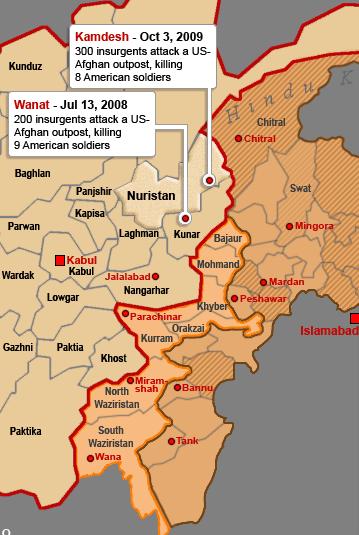
It’s a brave new world that the rulers envision, no doubt. No more conventional warfare, not even fourth generation warfare since the rulers know what we’re doing, who we are, where we are, what assets we have, to whom we’re connected, and how to stop “trouble-making” before it gets started. Iraq was a laboratory for stability operations, and the story about the “snake-eaters” using a synthesis of organic intelligence, signals intelligence and smart analysis and finding the bad guys in order to end the insurgency only plays into the hands of the collectivists. But can it really work like this?
The narrative about the “snake eaters” bringing an end to the campaign in Iraq is greatly overblown. It was primarily the U.S. Marines who brought stability to the Anbar Province, and it was the hard work of thousands of Soldiers in the balance of Iraq that brought the modicum of success that we had in Iraq, for what end I don’t really know.
The Chicago police department cannot even stop gang violence in their own city, and the Governor is considering the use of National Guard troops to quell the violence. It won’t work, and I seriously doubt that such troops would even be under arming orders, any more than the National Guard sent to the Southern border were under arming orders.
There is another intersection of this paradigm with collectivist intentions. In order to find money for redistribution to the masses, they need to gut the military. Notwithstanding the ongoing debate in our community over a standing army, the point is that the collectivists are going after money, and before they target 401Ks and IRAs, they willl use defense dollars in their designs for control. It’s easier for them that way.
But this is all well and good for the rulers until the bullets start flying. Obamacare was and continues to be a big deal. Confiscation of 401Ks and IRAs might be the event that pushes typical Americans over the edge. Watching the death of loved ones due to decisions by government death panels (while their wealth goes to funding the medical care of illegal aliens) might be another.
In the end, the hives the government has created (like Chicago) don’t work because they undermine values and the organic family unit. Whatever the final straw, if the government cannot control violence in the very hives that they’ve created, they certainly can’t accomplish that in suburbia America, where fences, yard dogs and guns every fifty yards would make the hedgerows in Normany look like inviting terrain.
To be sure, the degree of electronic control over Americans makes the situation hard, and the government knows almost everything about us. But for the Bilderberg group and the elitist rulers, I have a suggestion. Try a test case in which you announce gun and wealth confiscations, and send one of the many federal policing agencies up Highway 276 in South Carolina, through Marietta, and turn left on Highway 11. Within a few minutes make a turn to the right towards Jocassee Gorges, and start your confiscations up in those hills. My bet is that the your vehicles will be blown to smithereens. If you do make it up the road, it’s likely that they boys with scoped, bolt action hunting rifles will make life very difficult for you. With all due respect to the tactical trainers (which training is very good and necessary, I’m sure), there won’t be small unit maneuver warfare. No one will ever see the boys hiding behind the trees. They won’t go on the run as a lone wolf because you won’t ever know they were involved in anything. The best planning, the best troops and the best equipment couldn’t handle an insurgency in America – if one ever develops.
Or try to do confiscations in Murphy, North Carolina, or any one of a multitude of places in Idaho or Montana. To be reminded of the value of a good rifleman, I strongly recommend an article in the most recent American Rifleman magazine (October 2013). Sometimes this publication becomes annoying with its advertizing and product reviews. But occasionally the magazine crafts a winner, and this one is meets the criteria.
The article is entitled “Where will we bury them all?,” and in my paper copy it begins on page 95. It’s the story about the communist invasion of Finnland in 1939, and the value of basic combat rifles and good fieldcraft. It summarizes:
The winter war proved a costly victory for the Soviets. The Red Army lost approximately 126,875 dead or missing, 264,908 wounded and appriximately 5,600 captured. In addition, they lost about 2,268 armored vehicles. The Finns suffered greatly to preserve their freedom. In the four months of combat, Finnish losses numbered approximately 26,662 dead and more than 39,000 wounded. A tiny nation of riflemen had held off the communist Red giant.
It would be easy to conclude that the 50% of America which is still working is on a direct collision course with the elitist rulers. It would be just as easy for the collectivists to conclude that biometrics, numbers, cards, decryption, cameras and aggressive policing will enable their designs. The former conclusion seems more likely every day. The later conclusion seems dangerous for the collectivists.
Of course, everything in this article is for educational purposes only.